What is malware?
Learn about all the various computer viruses
Brief Summary
Malware is a type of software that is designed to harm your computer or steal your personal information without your permission. You can unintentionally install it by clicking on a wrong link or installing programs that contain malware.
The term malware is a combination of malicious and software. So basically, malware is software that is malicious with bad intent in regards to your personal information, computer, and operating system.
Malware is code developed by hackers created to cause damage and gain access to a network unauthorized. In addition, hackers use malware to gain access to financial information, healthcare records, passwords etc.
Hackers, also known as cyber attackers, attack computers with a link or file through an email that they send to their victims. If a victim clicks on the email, the process will begin. However, emails are not the only way hackers infect people with malware. Hackers also use text messages, infected apps, and software installation that is untrustworthy and fake, to mention a few.
What does malware do?
Various malware types cause damage today. These are:
- Virus
- Worms
- Spyware
- Trojans
- Ransomware
Below we’ve described what each type of malware does to cause damage to your computer.
What is a computer virus?
Usually, when one thinks of malware, they automatically also think of viruses. These two terms/meanings are not interchangeable.
A computer virus is an application that copies itself every time it attaches its code to other files on your system and computer.
The reason it’s called a virus is that the process is similar to viruses in the body. Just like how a cold infects the cells in your body when you get sick, the same process applies to a computer virus. We transfer our viruses to other people around us when we are contiguous, and the same pertains to computer viruses. The computer virus goes from one computer to another computer, damaging each infected computer.
Since viruses are easy to identify, most hackers do not use viruses to infect computers as there is software available today that would detect such a virus immediately. So keep in mind, while a computer virus is a type of malware, they are not interchangeable.
What is a computer worm?
A computer worm gets its name from the way they infect systems. The malicious software that’s a worm typically replicates itself from one computer to another; they weave their way through the network. A computer worm tries to connect to various machines to spread the infection continuously.
Computer worms are not similar to computer viruses. A computer virus, as mentioned above, targets one individual computer, whereas computer worms target networks of computers. Furthermore, unlike computer viruses, a computer worm does not need a host file to start attacking.
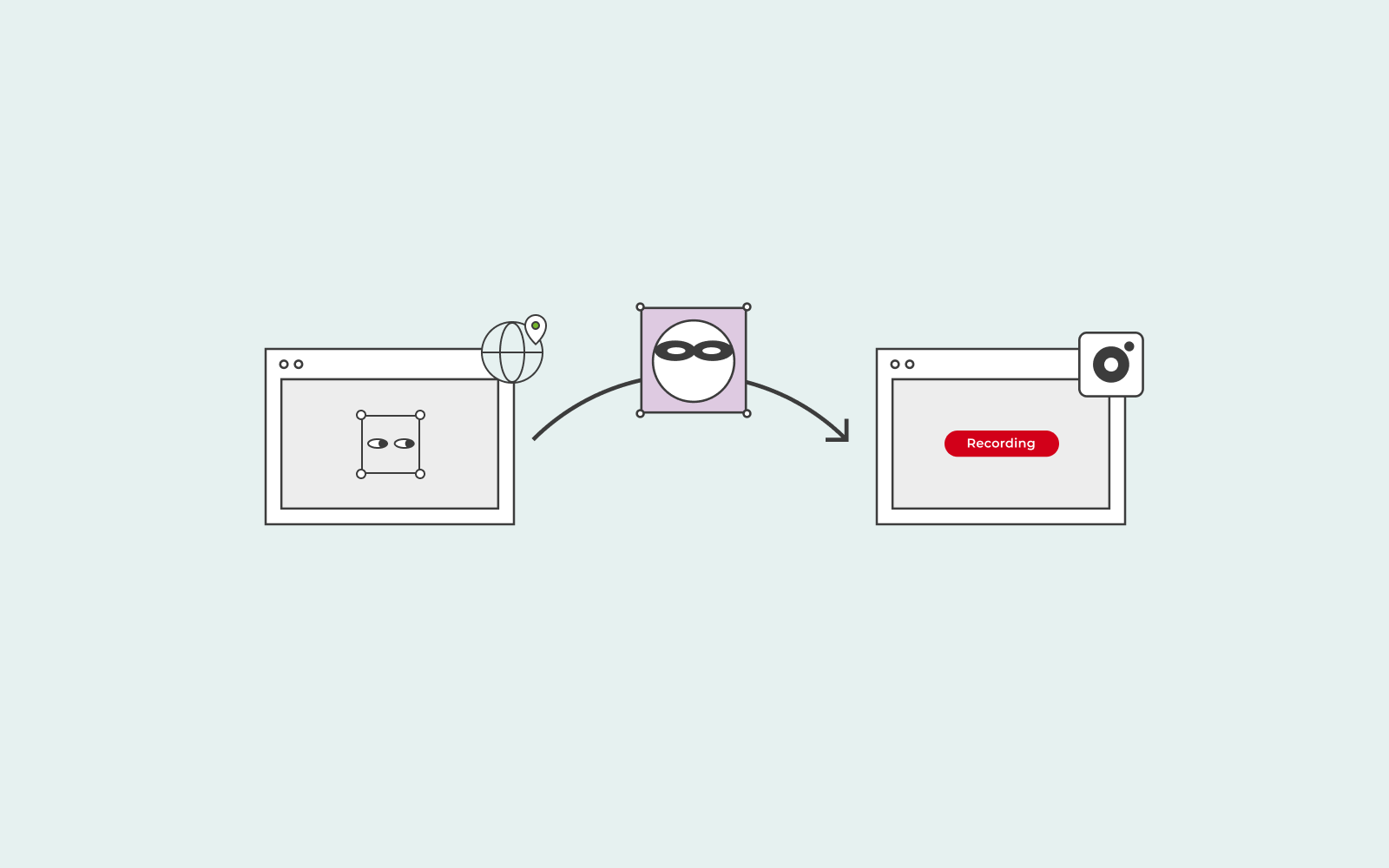
What is spyware?
Like the different types of malware we’ve described above, spyware is also designed to gather personal information from your computer, which they later use with bad intent. Hackers can use four different ways to infest your computer with spyware.
These four different ways are: through trojans, through interactions with adult content material and third-party program downloads, through exploiting and compromising tracking cookies, and finally through system monitors.
What is a trojan horse virus?
The Greeks decided to use a wooden trojan horse to enter Troy. Of course, as we’ve all heard the history, later that evening, several soldiers dropped out of the enormous wooden trojan horse and began to attack the city of Troy.
Trojan horse viruses are masters of disguise. Trojan horse viruses do an excellent job to make programs with malicious intent seem and look just like standard programs with good intent; they provide a good disguise.
Once you’ve downloaded the program that looks legitimate, the trojan horse virus releases malware that attacks your computer.
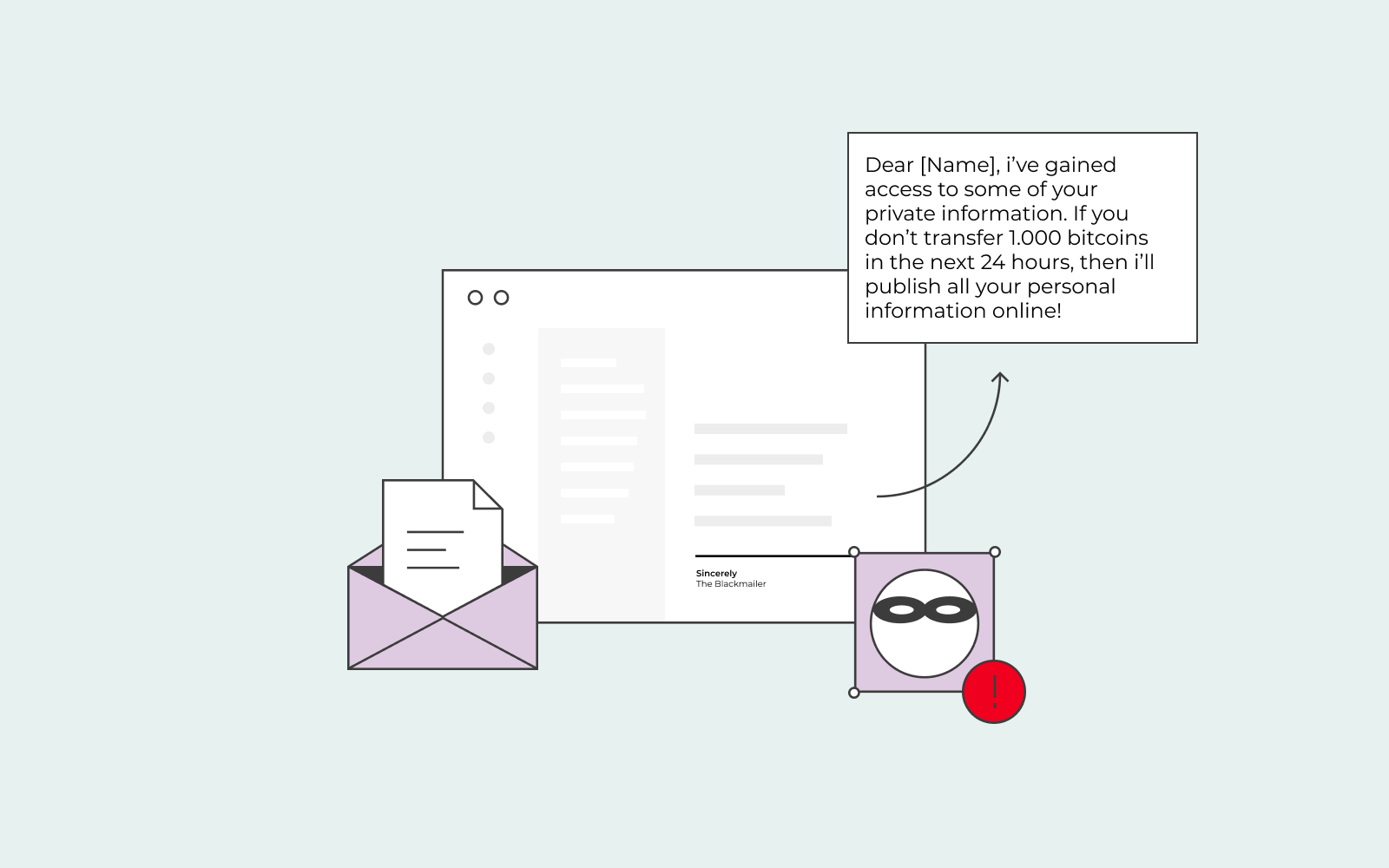
What is ransomware?
Ransomware works by blocking you from starting your computer. Instead, when you try to start your computer, all you’ll see is a big lock on your screen and a message with a threat that you need to pay the ransom.
Ransomware is a type of malware that doesn’t let you access your computer or even mobile device by encrypting the data until you’ve paid the sum of money or bitcoins that the hacker has asked for. It’s a dangerous type of malware and one that is spreading worldwide.
Ransomware can impact you through spam email, spear phishing (when a hacker targets an individual – read more about phishing), and watering hole attacks (when a hacker observes which website an organization uses and then infects it).
Protect yourself by avoiding scam emails and also by avoiding browsing websites that look phishy. Also, create a backup of your files, set up a good anti-virus and never pay the ransom.
Malware attack
Now that you know what malware is and the different types of malware, let’s discuss the various methods hackers use to perform a malware attack.
- Keyloggers
Keyloggers are similar to someone looking over your shoulder when you’re drawing money from an ATM. If you’ve accidentally clicked on a phishing email, you might have accidentally downloaded this keylogger which will record every password you use on your computer. And on occasion, the log will be sent to its owner to take advantage of your personal information.
- Phishing
We’ve mentioned phishing a few times, but that’s because it plays a significant role in malware attacks. Phishing is, as previously stated when you receive a spam email with a link or an attachment. It could also be a dubious website where you might accidentally click on something, and troublesome software will download and install in the background without you being aware of it.
- Malvertising
Malvertising has become popular among hackers and attackers. What hackers do is buy legitimate advertising space on trustworthy websites. However, these ads contain malicious code. You don’t even have to interact; the malware will download automatically and damage your computer.
How do you know a malware attack has impacted you?
If it’s not in the form of ransomware where you can’t access your computer due to the malware blocking you and asking for money, you’ll notice that you have malware when your computer runs slow, for example.
- It can be that you want to visit a website, but your browser keeps redirecting you to another website.
- If you have a problem with starting your computer and shutting down your computer, that might be a sign of malware.
- If you continuously receive a pop-up, your computer might be infected with malware.
In fact, browser redirect and pop-ups are the strongest indicators that you have malware.
How to prevent malware attacks?
- Firstly, the best way to prevent malware attacks is by closely monitoring your email inbox. Don’t open emails you don’t recognize, and if you do happen to open them, don’t download the files attached to the email and don’t click on the links shared in the email.
- Don’t click on pop-ups when you’re browsing a website. Also, be cautious, don’t visit questionable websites.
- Backup your files so that you can feel assured that all your files are saved in a hard drive, and you can access them in the unfortunate case of ransomware.
- Keep your computer and various systems up to date. Hackers tend to attack computers with older software, and that’s not as protected. Updates usually also provide you with protection.
Perhaps most importantly, get yourself an excellent anti-virus protection software. Anti-virus software will detect any virus that has entered your computer and will notify you immediately and delete the virus from your computer before it can harm you.
